Best encrypted file transfer software: Safeguard Your Data with Top Solutions
Exploring the realm of encrypted file transfer software unveils a world where data security takes center stage. In today's digital age, ensuring the confidentiality and integrity of sensitive information is paramount. Let's delve into the realm of the best encrypted file transfer software and discover the robust solutions that can protect your data from prying eyes and unauthorized access.
Overview of Encrypted File Transfer Software
Encrypted file transfer software is a type of application that enables users to securely send and receive files over the internet. This software uses encryption techniques to ensure that data is protected from unauthorized access during transit.
Using encrypted file transfer software is crucial to safeguard sensitive information and maintain data privacy. Without encryption, files sent over the internet are vulnerable to interception by hackers or malicious actors, putting confidential data at risk of exposure.
Importance of Using Encrypted File Transfer Software
- Protection of sensitive data: Encrypted file transfer software ensures that confidential information such as financial records, legal documents, and personal data remain secure during transmission.
- Compliance with regulations: Many industries require the use of encrypted file transfer software to comply with data protection regulations and maintain customer trust.
- Prevention of data breaches: Encrypting files before transferring them helps prevent unauthorized access and reduces the risk of data breaches that can lead to financial losses and reputational damage.
Examples of Situations Where Encrypted File Transfer Software is Crucial
- Healthcare: Healthcare organizations need to securely transfer patient records and medical data to ensure patient confidentiality and comply with HIPAA regulations.
- Legal: Law firms often deal with sensitive legal documents that must be protected from interception or unauthorized access when shared with clients or partners.
- Financial: Financial institutions transfer sensitive financial data such as account information and transaction details that require encryption to prevent fraud and unauthorized access.
Features to Look for in Encrypted File Transfer Software
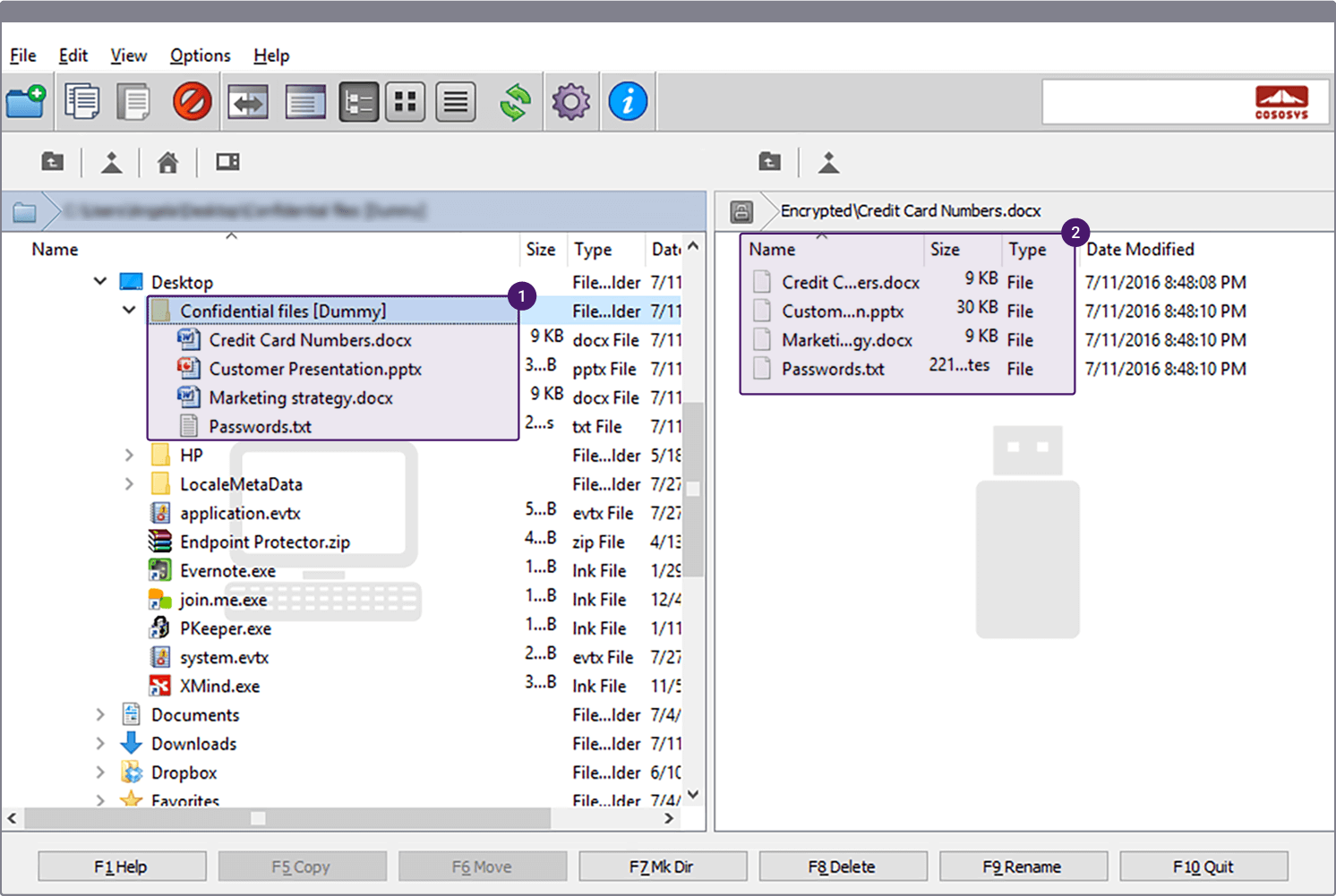
When choosing encrypted file transfer software, it is crucial to consider certain features that ensure the security and reliability of your file transfers. Here are some essential features to look for:
1. End-to-End Encryption
End-to-end encryption is a must-have feature in encrypted file transfer software. This encryption method ensures that data is encrypted on the sender's device and can only be decrypted by the intended recipient. It prevents anyone, including the service provider, from accessing the contents of the transferred files.
2. Secure Protocols
Look for software that supports secure protocols like SFTP (SSH File Transfer Protocol) or FTPS (FTP Secure). These protocols add an extra layer of security to your file transfers by encrypting data in transit.
3. Two-Factor Authentication
Two-factor authentication provides an additional security measure by requiring users to verify their identity with a second form of authentication, such as a code sent to their mobile device. This feature helps prevent unauthorized access to your files.
4. Audit Trails and Logs
Having audit trails and logs in your file transfer software allows you to track and monitor all file transfer activities. This feature is essential for compliance purposes and helps in identifying any unauthorized access or unusual activities.
5. File Size Limitations
Consider the file size limitations of the software, especially if you frequently transfer large files. Look for software that can handle the size of files you typically work with to ensure smooth and secure transfers.These features are crucial in ensuring the security and reliability of your file transfers.
When evaluating encrypted file transfer software, make sure to prioritize these key features to protect your sensitive data effectively.
Top Encrypted File Transfer Software Options
When it comes to choosing the best encrypted file transfer software, there are several options available in the market. These software solutions offer various features to ensure secure file transfers for individuals and businesses. Below is a comparison table highlighting some of the top encrypted file transfer software options, along with their key features, pricing, and user ratings.
Comparison Table of Encrypted File Transfer Software
| Software Name | Key Features | Pricing | User Ratings |
|---|---|---|---|
| 1. ProtonMail | End-to-end encryption, Secure file sharing, User-friendly interface | Free plan available, Premium plans starting at $5/month | 4.5/5 |
| 2. Tresorit | Zero-knowledge encryption, File versioning, Access control | Plans starting at $10.42/month | 4.7/5 |
| 3. Sync.com | End-to-end encryption, Secure file sharing, File recovery | Free plan available, Pro plans starting at $8/month | 4.6/5 |
Pros and Cons of Top Encrypted File Transfer Software
- ProtonMail:
- Pros:Offers end-to-end encryption for secure communication, user-friendly interface for easy use.
- Cons:Limited storage capacity in free plan, some advanced features available only in premium plans.
- Tresorit:
- Pros:Zero-knowledge encryption ensures maximum security, file versioning for easy tracking of changes.
- Cons:Higher pricing compared to some competitors, may be more complex for beginners.
- Sync.com:
- Pros:Secure file sharing with end-to-end encryption, file recovery feature for accidental deletions.
- Cons:Limited features in the free plan, pricing slightly higher than some alternatives.
Security Measures and Compliance
When it comes to encrypted file transfer software, ensuring data security is paramount. These programs use advanced encryption techniques to protect sensitive information during transfer, making it nearly impossible for unauthorized parties to access or intercept the data.
Data Encryption Protocols
Encrypted file transfer software commonly relies on encryption protocols to secure data during transmission. Some of the most widely used encryption protocols include:
- Secure Socket Layer (SSL): A standard security technology for establishing an encrypted link between a web server and a browser, ensuring data remains private and secure.
- Transport Layer Security (TLS): An updated version of SSL, TLS provides secure communication over a computer network, safeguarding data integrity and confidentiality.
- SSH File Transfer Protocol (SFTP): A secure file transfer protocol that encrypts both commands and data, protecting sensitive information from potential threats.
Compliance Standards
The best encrypted file transfer software adheres to stringent compliance standards to ensure the highest level of data security. Some of the key compliance standards that these programs typically follow include:
- General Data Protection Regulation (GDPR): Ensures the protection of personal data and privacy for individuals within the European Union.
- Health Insurance Portability and Accountability Act (HIPAA): Safeguards sensitive patient information to ensure the confidentiality and integrity of healthcare data.
- Sarbanes-Oxley Act (SOX): Imposes strict regulations on financial reporting to prevent corporate fraud and ensure the accuracy of financial disclosures.
Implementation and Integration
Implementing and integrating encrypted file transfer software is crucial for organizations looking to secure their data transfers. Here are some tips and best practices to ensure a smooth process:
Ease of Implementation
- Choose a user-friendly encrypted file transfer software that offers clear documentation and support.
- Consider cloud-based solutions that require minimal setup and maintenance.
- Ensure compatibility with your existing systems and software to avoid integration issues.
Tips for Integrating
- Start by conducting a thorough assessment of your current systems and workflows to identify integration points.
- Work closely with the software provider to customize the implementation according to your organization's needs.
- Train your staff on how to use the encrypted file transfer software effectively to maximize its benefits.
Best Practices for Smooth Integration
- Establish clear communication channels between your IT team and the software provider to address any integration challenges promptly.
- Regularly monitor and test the encrypted file transfer software to ensure it is functioning correctly and meeting security requirements.
- Implement a phased approach to integration, starting with smaller workflows or departments before scaling up to the entire organization.
Case Studies and Real-world Examples

Implementing encrypted file transfer software has proven to be crucial for organizations looking to secure their sensitive data. Let's explore some success stories of organizations that have benefited from using such software.
Healthcare Industry
- In the healthcare industry, a hospital implemented encrypted file transfer software to securely exchange patient records with external partners and specialists.
- By using encrypted file transfer software, the hospital ensured that patient data remained confidential and complied with healthcare regulations.
- This software solution helped the hospital streamline its processes while maintaining the highest level of security for sensitive information.
Financial Sector
- A financial institution integrated encrypted file transfer software to protect financial transactions and customer data during transfers.
- With this software in place, the organization significantly reduced the risk of data breaches and ensured compliance with financial regulations.
- The encrypted file transfer software enabled the financial institution to increase efficiency and trust among clients by safeguarding their sensitive information.
Government Agencies
- Government agencies have also benefited from encrypted file transfer software to securely exchange classified information and sensitive documents.
- By leveraging this software solution, government entities enhanced data security measures to prevent unauthorized access and data leaks.
- Encrypted file transfer software has played a vital role in protecting national security interests and maintaining the integrity of government operations.
Closing Notes
As we wrap up our discussion on the best encrypted file transfer software, it's evident that safeguarding your data is no longer an option but a necessity. Choosing the right software equipped with top-notch encryption methods can provide you with peace of mind and ensure that your confidential files remain secure during transit.
Take the proactive step of fortifying your data protection measures with these cutting-edge solutions.