Secure file transfer solutions for businesses: Ensuring Data Security and Compliance
In today's digital landscape, secure file transfer solutions are crucial for businesses to protect sensitive data and ensure regulatory compliance. This comprehensive guide delves into the various types of solutions available, essential features to look for, best implementation practices, and the importance of compliance with data protection regulations.
Let's explore how businesses can securely transfer files in an ever-evolving cybersecurity environment.
When it comes to safeguarding your company's data, having a robust file transfer solution is key. From cloud-based options to on-premises systems, understanding the nuances of secure file transfers is essential for modern businesses.
Types of Secure File Transfer Solutions

When it comes to secure file transfer solutions for businesses, there are various options available to ensure data protection and confidentiality. Two primary types are cloud-based solutions and on-premises solutions, each with its own set of advantages and considerations.
Cloud-Based Solutions
Cloud-based secure file transfer solutions involve storing and transferring files over the internet using a third-party service provider's infrastructure. These solutions offer scalability, accessibility from anywhere with an internet connection, and automatic updates for security features. However, businesses must trust the provider's security measures and may face potential risks related to data privacy and compliance.
On-Premises Solutions
On-premises secure file transfer solutions involve hosting and managing file transfers within a company's own infrastructure. This option provides businesses with greater control over data security and compliance, as well as the ability to customize and tailor the solution to specific needs.
However, it may require a higher initial investment in hardware and software, as well as ongoing maintenance and updates.
Importance of End-to-End Encryption
Regardless of the type of secure file transfer solution chosen, end-to-end encryption is crucial for ensuring data security. This encryption method protects data throughout the entire transfer process, from the sender to the recipient, making it virtually impossible for unauthorized parties to access or intercept the information.
By implementing end-to-end encryption, businesses can enhance the confidentiality and integrity of their sensitive files, mitigating the risk of data breaches and unauthorized access.
Features to Look for in Secure File Transfer Solutions
When selecting a secure file transfer solution for your business, it is crucial to consider a range of features that can enhance security and efficiency in file sharing. These features can help protect sensitive data and ensure compliance with regulations.
Access Controls and User Permissions
Access controls and user permissions play a vital role in ensuring the security of file transfers. By setting up granular access controls, businesses can restrict who can view, edit, or delete files, reducing the risk of unauthorized access. User permissions allow administrators to assign specific roles and privileges to users, ensuring that only authorized individuals can access sensitive information.
- Implement role-based access controls to assign permissions based on job roles and responsibilities.
- Enable two-factor authentication for an added layer of security when accessing files.
- Regularly review and update user permissions to align with changing business needs.
Audit Trails and Logging Capabilities
Audit trails and logging capabilities are essential features that help track file transfers and monitor user activity. By keeping a record of who accessed, modified, or shared files, businesses can easily identify any suspicious behavior and investigate potential security incidents.
Audit trails provide a detailed history of file transfers, allowing organizations to demonstrate compliance with regulatory requirements.
- Enable logging of all file transfer activities, including date, time, and user information.
- Configure alerts for unusual file transfer activities, such as large downloads or access from unknown locations.
- Regularly review audit logs to identify any anomalies or security breaches.
Implementation Best Practices

Implementing secure file transfer solutions within a business environment is crucial for maintaining data security and compliance
Steps for Implementing Secure File Transfer Solutions
- Conduct a thorough assessment of your organization's file transfer needs and requirements.
- Choose a secure file transfer solution that aligns with your business goals and complies with industry regulations.
- Develop a detailed implementation plan outlining timelines, responsibilities, and resources needed.
- Test the secure file transfer solution in a controlled environment before full deployment to ensure functionality and security.
- Train employees on how to use the secure file transfer solution effectively and securely.
Guidelines for Integrating Secure File Transfer Solutions with Existing IT Infrastructure
- Ensure compatibility with existing systems and applications to facilitate seamless integration.
- Work closely with IT teams to configure the secure file transfer solution to meet the organization's specific requirements.
- Establish protocols for data encryption, user authentication, and access control to maintain security standards.
- Monitor system performance and conduct regular audits to identify and address any vulnerabilities or issues.
Importance of Employee Training and Awareness
- Provide comprehensive training on secure file transfer practices to all employees who handle sensitive data.
- Emphasize the importance of following security protocols and best practices to prevent data breaches and unauthorized access.
- Implement regular security awareness programs to keep employees informed about the latest threats and security measures.
- Encourage a culture of security consciousness and accountability among all staff members to promote a secure file transfer environment.
Compliance and Regulatory Considerations
When it comes to secure file transfer solutions for businesses, compliance with data protection regulations is a crucial aspect to consider. These solutions play a vital role in helping businesses ensure data privacy and security while meeting the requirements set forth by various regulatory bodies.
Impact of GDPR, HIPAA, and Industry-Specific Regulations
Regulations such as GDPR (General Data Protection Regulation) and HIPAA (Health Insurance Portability and Accountability Act) have significantly impacted file transfer practices in various industries. These regulations require businesses to implement robust security measures to protect sensitive data during transfer.
- Under GDPR, businesses must ensure that personal data is transferred securely and with appropriate safeguards in place to protect against unauthorized access or disclosure.
- HIPAA regulations mandate that healthcare organizations use secure file transfer solutions to safeguard patient information and maintain compliance with data privacy requirements.
- Industry-specific regulations, such as PCI DSS (Payment Card Industry Data Security Standard) for the payment card industry, also emphasize the need for secure file transfer practices to protect financial data.
Ensuring Data Privacy and Security
Businesses can take several steps to ensure data privacy and security while meeting compliance requirements:
- Implementing end-to-end encryption to protect data in transit and at rest.
- Using secure protocols such as SFTP (Secure File Transfer Protocol) or HTTPS for transferring sensitive files.
- Implementing access controls and authentication mechanisms to restrict unauthorized access to files.
- Regularly auditing file transfer activities to ensure compliance with regulatory requirements and identify any potential security risks.
Concluding Remarks
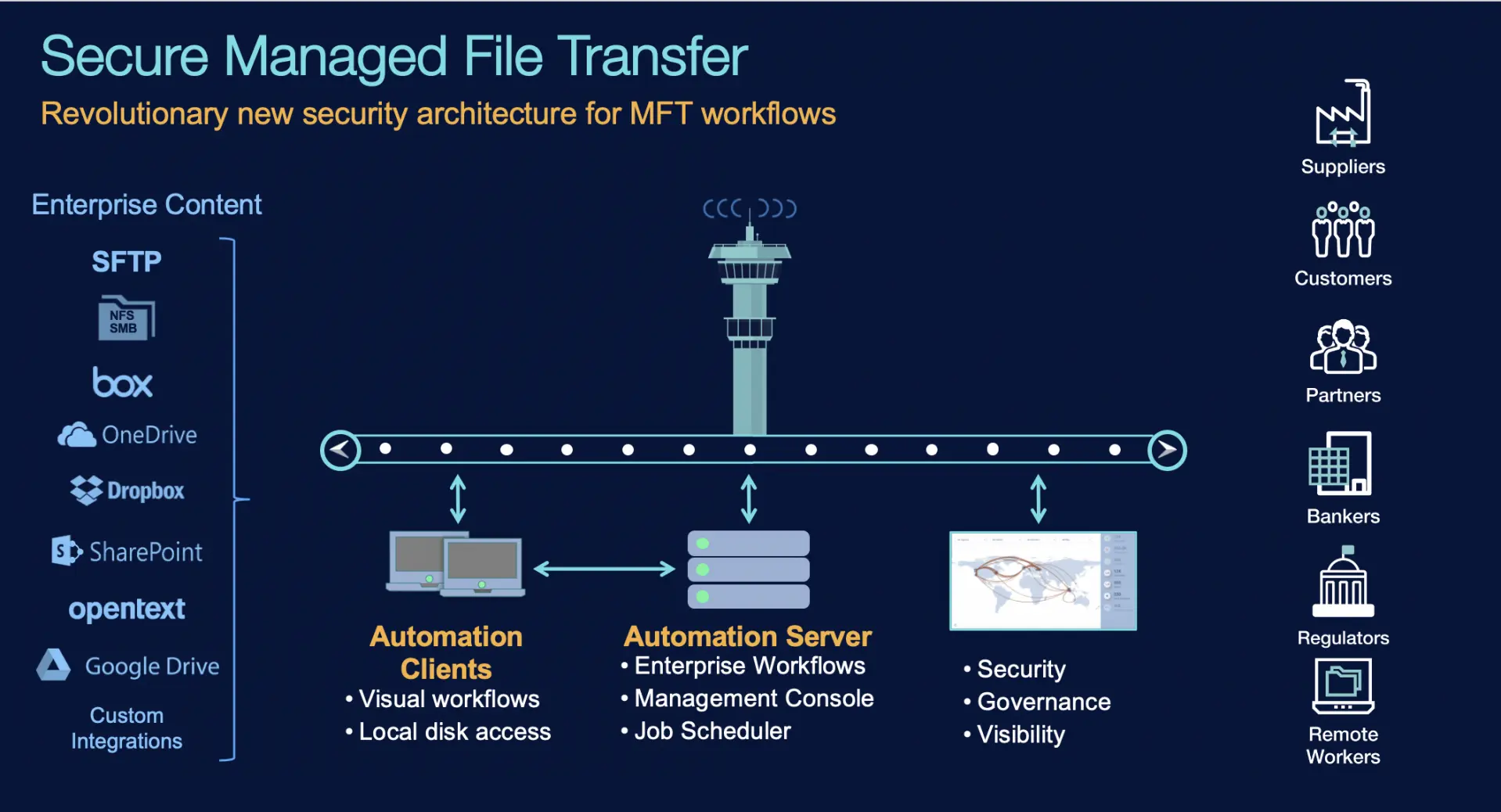
As we wrap up our discussion on secure file transfer solutions for businesses, it's evident that prioritizing data security and compliance is non-negotiable in today's digital age. By implementing the right tools and practices, businesses can safeguard their sensitive information and meet regulatory requirements effectively.
Stay vigilant, stay secure.